41 | Add to Reading ListSource URL: www-irma.u-strasbg.frLanguage: English - Date: 2013-04-28 09:35:52
|
|---|
42 | Add to Reading ListSource URL: people.mpim-bonn.mpg.deLanguage: English - Date: 2011-05-20 11:50:09
|
|---|
43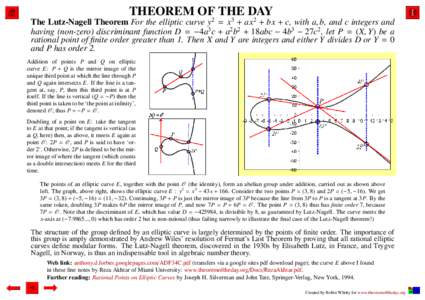 | Add to Reading ListSource URL: www.theoremoftheday.orgLanguage: English - Date: 2014-02-07 05:07:17
|
|---|
44 | Add to Reading ListSource URL: www.dgalindo.esLanguage: English - Date: 2007-11-26 10:35:53
|
|---|
45 | Add to Reading ListSource URL: www.hyperelliptic.orgLanguage: English - Date: 2008-09-27 14:59:29
|
|---|
46 | Add to Reading ListSource URL: fc15.ifca.aiLanguage: English - Date: 2015-01-11 00:32:41
|
|---|
47 | Add to Reading ListSource URL: www.cs.umd.eduLanguage: English - Date: 2014-06-30 10:38:30
|
|---|
48 | Add to Reading ListSource URL: www5.rz.rub.deLanguage: English - Date: 2012-07-23 07:34:30
|
|---|
49 | Add to Reading ListSource URL: www.math.brown.eduLanguage: English - Date: 2006-10-31 13:20:17
|
|---|
50 | Add to Reading ListSource URL: www.ietf.orgLanguage: English - Date: 2015-07-23 10:29:05
|
|---|